Achieve Organization Continuity With Secure Cloud Storage Space Services
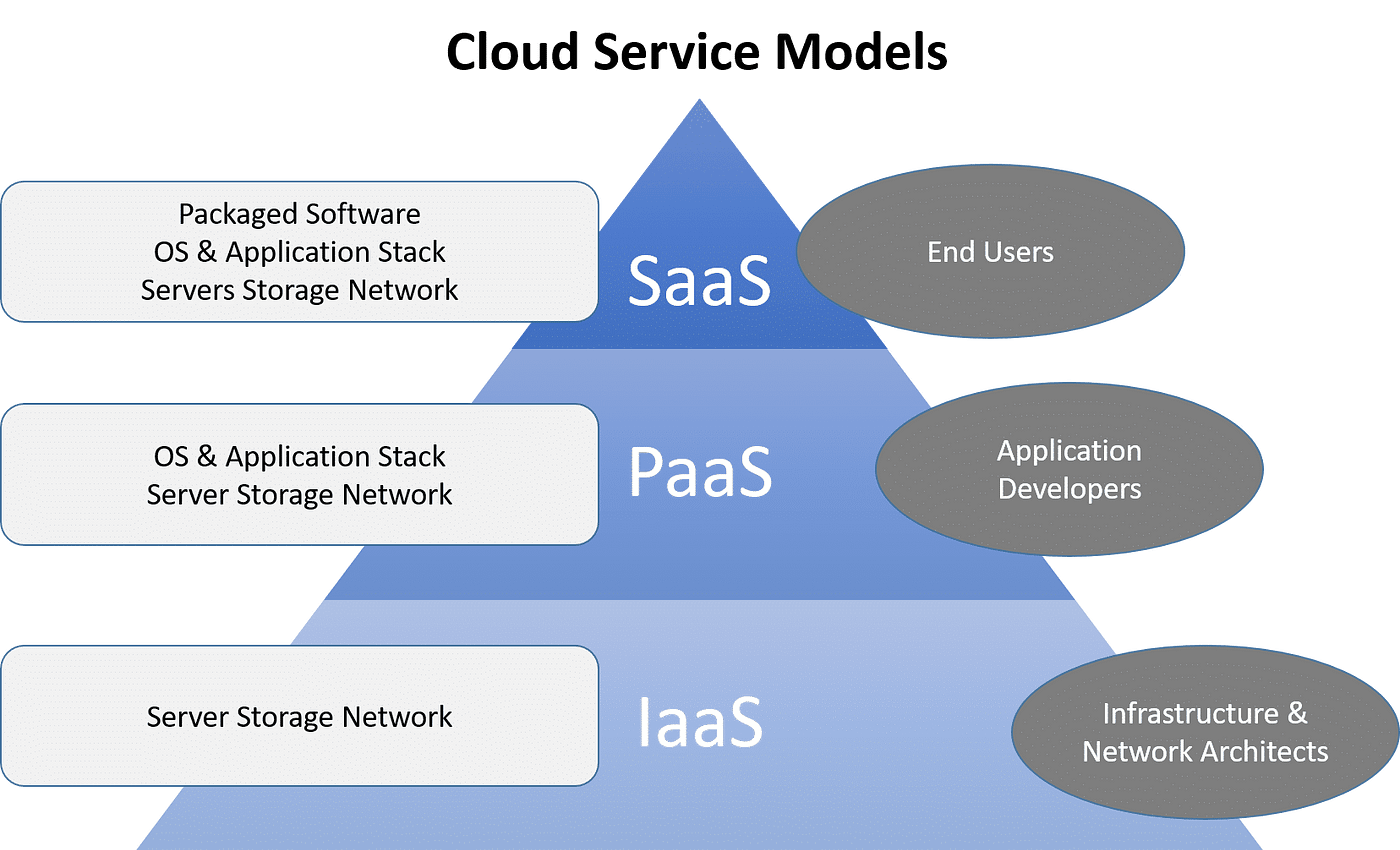
Benefits of Secure Cloud Storage
Undoubtedly, protected cloud storage supplies organizations a plethora of advantages in terms of data protection and ease of access. By keeping information on trusted cloud systems that employ security and advanced safety and security actions, businesses can protect their info from unapproved access or cyber risks. Overall, the advantages of safe and secure cloud storage translate into boosted data administration, enhanced operational performance, and boosted security for companies of all dimensions.
Secret Features for Company Continuity
By distributing information throughout different web servers or data facilities, organizations can alleviate the danger of data loss and ensure continual access to their details. In general, these crucial attributes function with each other to create a detailed organization connection method that safeguards important data and operations.
Importance of Data Security
In today's interconnected electronic landscape, securing delicate info is critical, making the importance of information file encryption a basic element of preserving data integrity and security. Data security involves inscribing details as if just licensed parties can access and decipher it. By transforming data into a secure layout, security functions as a shield versus unapproved access, lowering the risk of data violations and cyber risks.
Disaster Healing Techniques
Effective calamity recuperation approaches are crucial for services to ensure and minimize prospective interruptions continuity despite unforeseen events. A robust catastrophe recovery strategy entails describing procedures to recover data, applications, and IT framework in case of a catastrophe. One crucial facet of an efficient method is routine data backups. By storing data in safe and secure cloud storage solutions, services can ensure that crucial details is shielded and quickly available in situation of a calamity. Checking the calamity recuperation strategy consistently is also essential to determine any weak points and make needed improvements. Furthermore, having a marked group accountable for implementing the recovery strategy can simplify the procedure and minimize downtime. It is essential to consider various disaster situations and customize the recovery strategies to resolve specific threats that business may encounter. By carrying out extensive disaster recovery strategies, companies can boost their strength and secure their operations versus unpredicted events.
Selecting the Right Service Provider
To make certain try this site seamless organization continuity and reliable catastrophe healing, choosing a suitable and trusted company for protected cloud storage space is critical. When picking a cloud storage company, several key aspects should be considered. Examine the service provider's security steps. Guarantee they use durable encryption approaches, have stringent access controls, and abide by sector policies to protect your information. Additionally, analyze the company's information recuperation capacities. A credible company need to offer routine back-ups, redundancy procedures, and reliable healing procedures to minimize downtime in situation of a calamity.
Your organization needs may progress over time, so it's necessary to choose a supplier that can fit your expanding storage needs and adapt to transforming circumstances. By thoroughly reviewing these factors, you can select a cloud storage solution supplier that aligns with your organization's needs and makes certain continuous procedures in the face of possible disturbances.
Verdict
In verdict, safe and secure cloud storage space services great post to read provide crucial benefits for attaining company continuity, including improved safety and security attributes, smooth scalability, reliable collaboration tools, robust information back-up mechanisms, and catastrophe recovery approaches. Information file encryption plays a critical function in safeguarding delicate details, while selecting the appropriate company is vital to guaranteeing conformity with regulations and keeping functional effectiveness. linkdaddy cloud services. Safe and secure cloud storage is a beneficial possession in today's electronic landscape for making certain undisturbed service operations
Information backup systems are essential for protecting against data loss due to system failings, cyber-attacks, or human errors. By distributing information throughout numerous web servers or data facilities, companies can alleviate the threat of data loss and make certain continuous access to their details.In today's interconnected electronic landscape, safeguarding sensitive details is critical, making the significance of data file encryption a basic facet of maintaining information integrity and security. By converting information into a safe format, security acts as a guard versus unauthorized gain access to, lowering the threat of data violations and cyber risks.
Compliance requirements and data defense you can try this out laws often mandate the usage of encryption to protect sensitive information, emphasizing its critical duty in modern-day information safety and security techniques.
 Robert Downey Jr. Then & Now!
Robert Downey Jr. Then & Now! Charlie Korsmo Then & Now!
Charlie Korsmo Then & Now! Jurnee Smollett Then & Now!
Jurnee Smollett Then & Now! Michael C. Maronna Then & Now!
Michael C. Maronna Then & Now! Catherine Bach Then & Now!
Catherine Bach Then & Now!